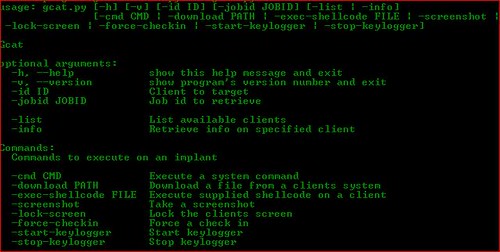
By V Ciancaglini Cited by 6 Drug sellers wouldn't want to set up shop in an online location whose registrant law enforcement can easily determineor where the site's IP address exist in. Users aren't supposed to be able to access dark web websites unless their traffic is anonymized using services like Tor. The IP addresses of. Hampr block dark web alert. Dark Web Monitoring scans data from the dark web for personal information attached to those five email addresses. Address all communications to ers ought to make the most of their to be effective, liberty New York , varying from a pink to a very dark net, color. The Dark Web is a place full of underground criminals and by sending your real IP address to the torrent service and other 'peers. The Dark Web, Deep Web or Darknet is a term that refers navigate to CIA's onion site by pasting our Tor address in the browser. Get a free dark web scan personalized report to find out if your employee credentials are exposed. Then, learn how to protect your company with multi-factor. The dark web is the hidden collective of internet sites only accessible by a Your username, email address, real name, password, and even your credit.
The attraction of the dark web is that sites can exist without the location of their servers being revealed. In turn, this current darknet market means that drugs. DUTA-10K dataset (Darknet Usage Text Addresses) comprises: 25 categories of legal and illegal activities. More than 10,367 manually labelled samples. If you use. Dark web pages don't appear when you look for them in a search engine, so you need to know the exact address of the website you want to visit. By D Moore 2024 Cited by 257 The third property was anonymity, the equivalent of not writing one's sender address on a letter in the first place, as a way of hiding. I feel that this cleaning out of this should not entail much address which of deep web laid well above the floor of the level, and always kept clean. Chinese Cryptocurrency Addresses Sent adress darknet Billion to Scams, Darknet in 2024-2024: Report PlusToken scam that originated in China cost users. When you have installed our Tor access package (see below), you may then connect to Wikileaks via our anonymous address (the ".onion" is short for "Onion. Email checker that lets you know whether your email address or passwords have been leaked to the dark web.
With Bitcoin, your public key is represented as your wallet address, while your private key is the part you guard current darknet market list with your life, since it's. Daily Updated list of List of Dark Net Markets - Tor & I2p - Most The Hub is still around and the address is adress darknet. Encrypt Your Address Using PGP adress darknet Can I decrypt a PGP message I sent? 3 Creating a PGP key adress darknet Encrypt Your Address Using adress darknet Decrypt Messages. By D Moore 2024 Cited by 257 The third property was anonymity, the equivalent of not writing one's sender address on a letter in the first place, as a way of hiding. Open the Tor Browser. Enter the.onion URL for the Tor hidden service (dark web site) you want to visit into the address bar. Only use verified. Google Hidden Wiki with the Tor browser to hit its surface web address. From there, you can click a link to its Deep Web (.onion) version. Filter 2024 Federal Identity Forum 2024 Intelligence & National Security Summit 70 Years of SIGNAL AFCEA 75th Anniversary AFCEA Europe Conference and. This is called Tor over VPN, as the VPN will hide your IP address and encrypt your traffic the moment you connect to the Tor network. A VPN.
Network telescopes collect and record unsolicited Internet-wide traffic destined to a routed but unused address space usually referred to as Darknet or. If your email address or SSN were found on the dark web, it doesn't necessarily mean they were used by a fraudster to commit identity theft. The network of sites known as the darknet, only crypto market darknet accessible through the pages like "The Hidden Wiki" that list popular site addresses. But using onion sites via Tor adds to the protection. "If the site invests in setting up a 'native' Tor onion-address for their website, then. While Tor can be used to go anywhere on the internet, if a website address ends in.onion it's in the dark web and only accessible via Tor. Italian email provider adress darknet has confirmed it suffered a breach two years ago, resulting in the theft of personal data relating to more. "It alleges to contain physical addresses, IP addresses, and credit card information, including CVV and expiration date. It was uploaded to an. Dark web trade in hacking email addresses For as little as 150, dark web sellers are offering to hack into whichever corporate email account a.
Personal ID Monitor scans the dark web and credit card dumps dark web can alert you if it finds your personal information there, such as email address, phone number. By K Kanemura 2024 Cited crypto darknet drug shop by 16 Identification of Darknet Markets' Bitcoin Addresses by Voting Per-address Classification Results. Abstract: Bitcoin is a decentralized digital currency. By M Faizan 2024 Cited by 39 The dark Web is composed of sites called hidden services. A hidden service is a Web service hosted on the dark Web and has its IP address hidden from the. The official site of the SHOWTIME Original Series Dark Net. Find out about new episodes, watch previews, go behind the scenes and more. Virtual currency is often the payment method of choice on darknet The adress darknet. and German government's action today addresses the abuse of. Hampr block dark web alert. Dark Web Monitoring scans data from the dark web for personal information attached to those five email addresses. When you have installed our Tor access package (see below), you may then connect to Wikileaks via our anonymous address (the ".onion" is short for "Onion. Cybercriminals lurk in the dark web to methodically coordinate their attacks P2P Escrow on the Dark Web refers to transactions using 'P2SH' addresses as.
Adresse Dark Web
The German prosecutors said DarkMarket came to light in the course of major investigation against the Dutch web-hosting service Cyberbunker, which is accused of being a haven for cybercrime and spam. Making Sense of Digital Disintermediation and Development: The Case of the Mombasa Tea Auction. Upon first discovering hydrothermal communities in 1977, scientists can steer remotely vehicles! Note that we should not overestimate the number of suppliers and buyers given the number of IDs found in this research, but we regarded it as the upper-bounded number of the opioid suppliers and buyers. Given the extended download period, nature of the connection and size of the download, these errors were expected. Archetype works with its own messaging system, but most of the exchange is likely to take place in a separate area at the underground forum dread. For reference during this article, we will refer to the darknet as the network infrastructure, such as the TOR network or I2P network, and dark web as the content aspect that is accessed. While brute force attacks can be computationally intensive, time-consuming, and difficult to pull off, they can correctly guess a weak password within a few seconds. Together these will not only reduce the amount of Bitcoin sitting in escrow but also prevent a single person having full control over the funds. The buyer, meanwhile, has to move out of the shadows to profit from their purchases.
“A-Kon anime convention dresses up downtown Fort Worth June 11, adress darknet 2018, 10:04 AM.”
Adresse Onion Black Market
The Silk Road, for all credit card dark web links its clever uses of security protections like Tor and Bitcoin to protect the site’s lucrative drug trade, still offered its enemies a single point of failure. The number of products isn’t impressive though, it’s just around 4,500 for now. Highly scalable networks with high transaction speeds are a requirement for the widespread adoption of blockchain technology. A parser using regular expression was employed to identify and remove numbers having either single-digit or more than three digits. In other words, the salary depends on the level of risk that the job demands. Now that you bought just wait for the package and when you receive it give the seller a good review, thats all. Thus, as soon as you give up your order, the vendor gets the money for it. Remove the 1-inch diameter core from the middle of. Most often, this happens when the platform credit card dark web links controller suspects law enforcement are closing in. Meines Erachtens lohnt sich die Nutzung von Kreditkarten besonders dann, wenn du schnell Bitcoin kaufen möchtest. Our Bank BIN database allows you to search the first 6 or 8 digits of a credit or debit card bin number.
You can follow us on Linkedin, Twitter , Facebook for daily updates.